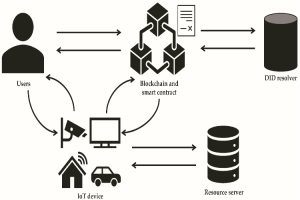
 In the digital age, where personal information is constantly transmitted and stored, ensuring the authenticity and security of individuals’ identities is paramount. Unique registration identifiers have emerged as a cornerstone in this endeavor, providing a robust mechanism for authentication and verification across various domains. These identifiers, often composed of alphanumeric characters or specialized codes, serve as distinctive markers tied to individuals or entities, facilitating seamless interactions while mitigating the risk of identity theft and fraud.
In the digital age, where personal information is constantly transmitted and stored, ensuring the authenticity and security of individuals’ identities is paramount. Unique registration identifiers have emerged as a cornerstone in this endeavor, providing a robust mechanism for authentication and verification across various domains. These identifiers, often composed of alphanumeric characters or specialized codes, serve as distinctive markers tied to individuals or entities, facilitating seamless interactions while mitigating the risk of identity theft and fraud.
Unlike traditional identifiers like usernames or passwords, which can be easily compromised or replicated, unique registration identifiers offer a higher level of security and reliability. By leveraging advanced encryption techniques and stringent validation protocols, these identifiers enable organizations to establish trust and confidence in their digital transactions and services.
Furthermore, unique registration identifiers pave the way for innovative approaches to identity management, including biometric authentication and blockchain technology integration. These advancements not only enhance security but also streamline processes, reducing friction in user experiences while safeguarding sensitive information.
As society increasingly relies on digital platforms for communication, commerce, and collaboration, the importance of robust identity verification mechanisms cannot be overstated. Through the adoption and refinement of unique registration identifiers, we can fortify our digital infrastructure, ensuring a safer and more trustworthy online ecosystem for all.
Fortifying Our Digital Infrastructure: Strengthening Security with Unique Registration Identifiers
In today’s interconnected world, where cyber threats loom large and data breaches pose significant risks, fortifying our digital infrastructure is imperative to safeguarding sensitive information and ensuring the integrity of online interactions. Unique registration identifiers stand as a cornerstone in this effort, offering enhanced security measures and robust authentication mechanisms across various digital platforms.
Enhancing Authentication Protocols
Unique registration identifiers serve as powerful tools in bolstering authentication protocols. Unlike conventional usernames and passwords, which are susceptible to brute-force attacks and phishing scams, these identifiers employ sophisticated encryption techniques and multi-factor authentication methods to verify users’ identities securely. By incorporating biometric data, such as fingerprints or facial recognition, into the registration process, organizations can establish airtight authentication procedures, thwarting unauthorized access attempts and safeguarding sensitive data.
Mitigating Identity Theft and Fraud
Identity theft and fraud remain pervasive threats in the digital realm, jeopardizing individuals’ financial security and eroding trust in online transactions. Unique registration identifiers play a pivotal role in mitigating these risks by providing a reliable means of verifying users’ identities. Through stringent validation processes and real-time monitoring capabilities, organizations can detect suspicious activities and flag potentially fraudulent transactions, minimizing the impact of cybercrime and protecting consumers from financial losses.
Streamlining Regulatory Compliance
In an increasingly regulated landscape, compliance with data protection laws and industry standards is paramount for organizations operating in digital environments. Unique registration identifiers facilitate compliance efforts by enabling organizations to track and audit user activities effectively. By maintaining comprehensive records of user interactions and access privileges, organizations can demonstrate compliance with regulatory requirements, mitigate legal risks, and uphold the trust and confidence of stakeholders.
Fostering Innovation in Identity Management
As technology continues to evolve, so too do the possibilities for innovation in identity management. Unique registration identifiers pave the way for groundbreaking advancements, such as blockchain-based identity solutions and decentralized authentication frameworks. By harnessing the power of distributed ledger technology and cryptographic principles, organizations can revolutionize the way identity is managed and authenticated, ushering in a new era of security and trust in the digital domain.
In essence, fortifying our digital infrastructure with unique registration identifiers is essential for safeguarding sensitive information, combating cyber threats, and fostering trust in online interactions. By prioritizing security and embracing innovative approaches to identity management, we can build a more resilient and trustworthy digital ecosystem for the future.
Building a More Resilient and Trustworthy Digital Ecosystem for the Future
- In an era defined by rapid technological advancement and pervasive digital connectivity, the imperative to construct a resilient and trustworthy digital ecosystem has never been more pressing. Achieving this goal requires a multifaceted approach that addresses the complex challenges of cybersecurity, data privacy, and trust in digital interactions.
- Central to this endeavor is the implementation of robust security measures, anchored by advanced encryption techniques and authentication protocols. By integrating cutting-edge technologies such as biometrics and blockchain, organizations can fortify their defenses against cyber threats and mitigate the risk of data breaches, fostering a more secure digital environment for users.
- Furthermore, prioritizing transparency and accountability is essential for instilling trust in the digital ecosystem. Organizations must adopt practices that promote data transparency, such as clear privacy policies and consent mechanisms, empowering users to make informed decisions about their personal information. Additionally, embracing principles of ethical data handling and responsible AI deployment can help mitigate concerns about algorithmic bias and data misuse, bolstering trust in digital systems and services.
- Collaboration and information sharing are also critical components of building a resilient digital ecosystem. By fostering partnerships between industry stakeholders, government agencies, and cybersecurity experts, we can enhance threat intelligence sharing, identify emerging risks, and collectively respond to cyber incidents, strengthening our collective defense against cyber threats.
- Ultimately, building a more resilient and trustworthy digital ecosystem requires a concerted effort from all stakeholders, including governments, businesses, and individuals. By investing in robust security measures, promoting transparency and accountability, and fostering collaboration, we can pave the way for a safer and more trustworthy digital future, where innovation thrives and users can engage with confidence in the digital world.
Conclusion
In conclusion, as we navigate the complexities of the digital age, building a resilient and trustworthy digital ecosystem is paramount to ensuring the security and integrity of our online interactions. By leveraging advanced technologies, promoting transparency and accountability, and fostering collaboration among stakeholders, we can create a safer and more reliable digital environment for all. It is through collective effort and unwavering commitment to cyber security principles that we can mitigate risks, instill trust, and pave the way for a future where individuals and organizations can confidently embrace the opportunities afforded by the digital realm.
Disclaimer: “This article is for educational & entertainment purposes.”
